Two of our partners have created a DDoS Attack Map. They have done this to visualise where digital threat incidents are located. These maps are a valuable tool that provide information on how to stay ahead of attacks.
Arbor conducts ongoing, Internet-wide research on today’s most critical network security and management challenges
Arbor Networks has collaborated with Google Ideas to create a data visualisation that shows what a global problem Distributed Denial of Service (DDoS) attacks have become. Google Ideas used anonymous data from Arbor Networks’ ATLAS global threat monitoring system to build a data visualisation that allows users to explore historical trends in DDoS attacks, and make the connection to related news events on any given day. The data is updated daily, and historical data can be viewed for all countries.
Video: Usage of the digital attack map
Alternative: A10 Networks live DDoS Attack World Map
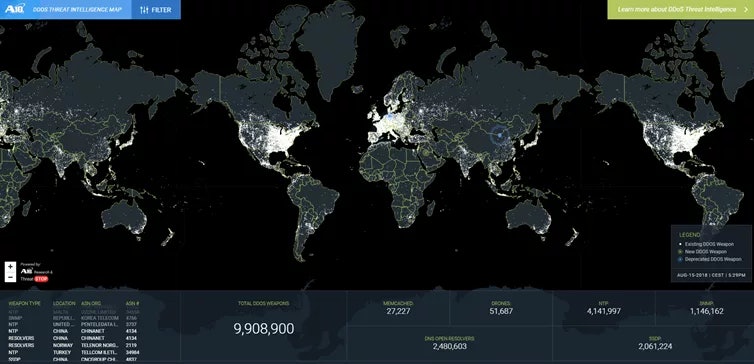
A10 Networks has created the DDoS Threat Intelligence Map. This attack world map helps you to visualise the DDoS threat landscape and to prepare for potential next waves of DDoS attacks against IT infrastructures. Unique to the A10’s DDoS map is that it gives you insights into where the next DDoS attacks will come from. With A10’s actionable DDoS threat intelligence platform, Thunder TPS, threat knowledge and insights are combined to facilitate a proactive approach to your DDoS protection.
What can you learn from the DDoS threat intelligence maps?
You may not always know why or when a DDoS attack is going to come. Knowing where the weapons are, means building a more effective defence. A10’s DDoS Threat Intelligence service identifies millions of IP addresses commonly used as agents for DDoS attacks.
This A10 Networks map includes large class-lists of threat objects with millions of entries that can be dynamically updated, making threat intelligence proactively actionable. This threat intelligence includes sprawling IoT botnets, IP addresses of reflection attack agents, and DDoS botnets actively used in the last 24 hours.
You can choose the categories of attack agents that you want to view, such as DNS or drone agents, see the geolocation of potential attacking elements, and check out entries that have been newly identified or deprecated from the snapshot of the near real-time DDoS threat feed.
Related solutions
Understanding the basics of cybersecurity
Get your copy of this 70+ pages whitepaper, to learn more about cybersecurity and to feel comfortable in a security conversation. Or get in touch with us directly if you find this topic of interest.