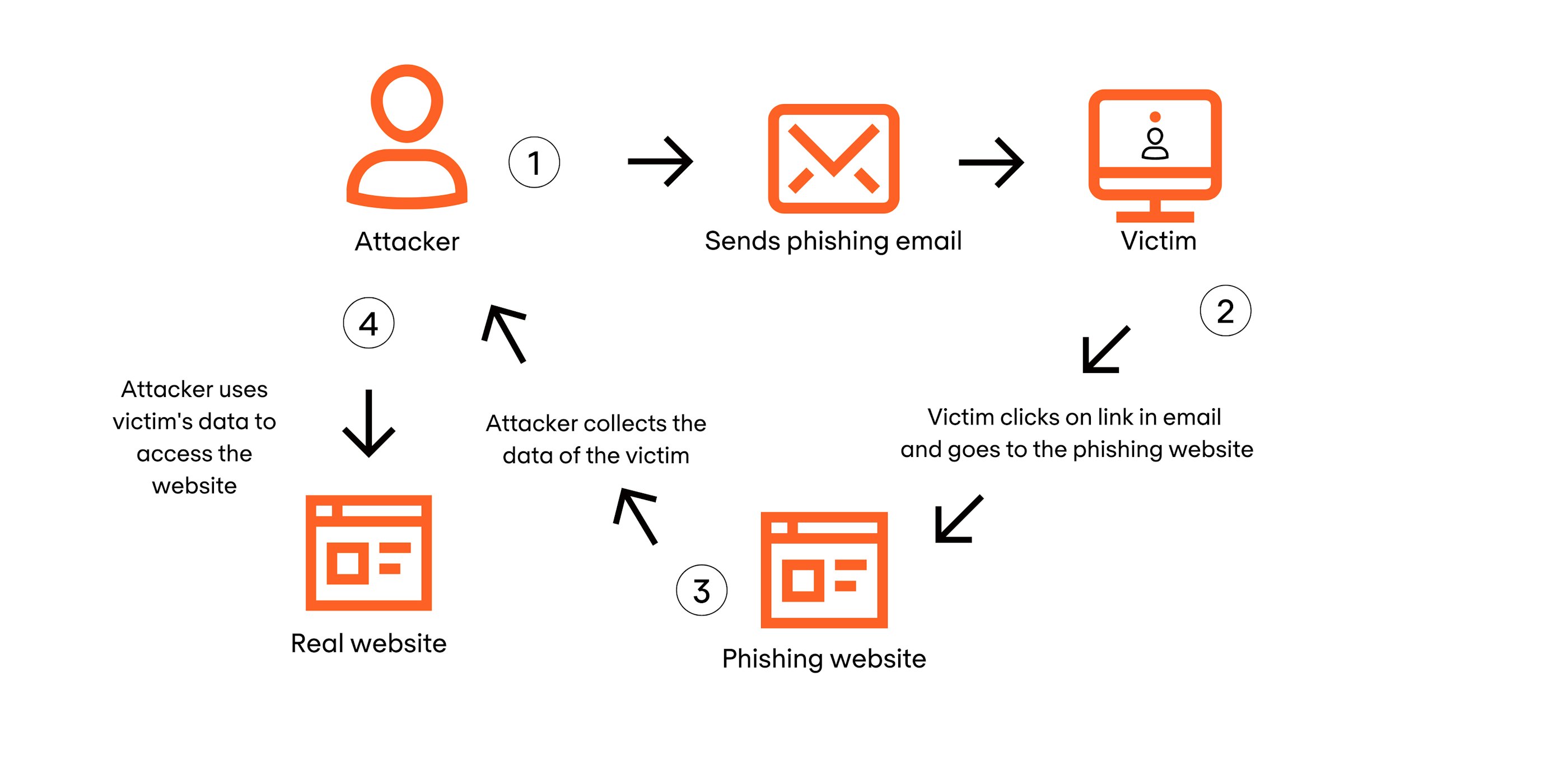
Phishing is a technique used by cybercriminals. By replicating a website, they obtain login details. These can include login credentials for an email account, computer network, or internet banking. What happens with this information varies depending on the situation.
Phishing is a social engineering tactic. It operates through websites that resemble the organisation they are impersonating. Cybercriminals recreate these websites as convincingly as possible. The URL of the phishing site often appears similar to the genuine URL. There are several ways you might be lured to such a page:
- Email: This is the most common method used to direct victims to a phishing site. Phishing emails often exploit urgency, time pressure, and current topics, such as the COVID-19 crisis. In businesses, phishing via email is called Business Email Compromise (BEC).
- Advertisements: Phishers can purchase advertisements on search engines like Google or Bing. Many people click on the top search results. If this is the phisher's advertisement, someone might unintentionally end up on the phishing site.
- Social media: Social media channels are used to obtain personal information.
- SMS: This form of phishing is also known as "smishing." It involves sending a shortened link in an SMS message. By opening this link on a smartphone, you end up on a phishing site.
What do phishers do with my data?
Once a cybercriminal acquires your data through a phishing page, they use it to log in to the real website. In the case of bank details, the criminal gains access to your bank account. Nowadays, companies and organisations are implementing additional authentication steps to enhance the security of bank accounts, for example. However, cybercriminals evolve rapidly and continuously devise new ways to bypass or hack this authentication.
These are no longer pages that simply ask for a username and password. When you enter your information on the phishing page, the criminal immediately logs in to your bank while you are still waiting on the phishing site. If the criminal is asked for verification, they send a message to you through the phishing site. So, you receive a message instructing you to verify your login, for example, via an SMS.
How does phishing work technically?
Behind a phishing site, there is a phishing panel. This panel operates on the infrastructure of the criminals. They can either host this panel themselves or use a hacked website. In the panel, the criminal can view all the collected data. When a new person enters their information on a phishing site, the attacker receives a pop-up displaying the same sensitive information.
In the past, criminals had to develop phishing panels themselves, but nowadays, they can purchase a ready-made phishing kit from the dark net. This can cost as little as a few tens of pounds. As a result, a criminal doesn't need to be an experienced programmer. They can install the kit themselves using a step-by-step guide, after which the phishing site becomes immediately active.
Why is phishing so prevalent?
Unlike malware attacks like ransomware, phishing does not require a criminal to possess extensive technical knowledge to get started. In a ransomware attack, a criminal hacks into a network and then distributes the malware to all computers within the network. Meanwhile, they must stay under the radar to avoid detection with their malware and proceed to encrypt all computers, including backups. This is just a brief description, but executing a ransomware attack is complex.
On the other hand, phishing is much simpler for criminals. They can purchase a phishing kit from the dark net, follow a step-by-step guide, and manipulate invoices. As a criminal, you don't even need to speak proper Dutch to manipulate invoices effectively.
Bank customers have been targeted by phishing for many years. Banks invest significant amounts of money and time to prevent their customers from falling victim to this attack method. For many other organisations, phishing might be a less familiar phenomenon, but it is indeed a real threat. Read this blog to learn how you can protect your organisation against phishing.
Phishing in numbers
Key findings based on a survey of 7,500 users and 1,050 security professionals from the 2024 State of the Phish report by Proofpoint.
Solutions to help you prevent phishing attacks
Our team is ready for you
Do you want to know more about this topic? Leave a message or your number and we'll call you back. We are looking forward to helping you further.
Continue reading

Cybersecurity Hospitality
Protect your hotel and guests with a strong cybersecurity strategy
Hotels and accommodation providers process sensitive data on a daily basis and are an attractive target for cybercriminals. Discover how a strong cybersecurity strategy can protect your hotel and guests against data breaches, ransomware and other threats.

Marcel Hoogendoorn

SOC NOC
NOC vs SOC: The difference and why do you need both?
Discover the difference between an NOC and SOC, and why the collaboration between network management and cybersecurity is crucial for stable and secure IT environments.


Fortinet NGFW
Fortinet introduces new FortiGate 30G, 50G, and 70G firewalls
Fortinet launches FortiGate 30G, 50G, and 70G firewalls, offering AI-driven security, high performance, and energy efficiency for distributed organisations.