What is vulnerability management?
Vulnerability Management is a proactive strategy that consists of identifying, prioritising and correcting the weaknesses and vulnerabilities of a company's security. The objective is to protect the IT (information system), but also the networks, applications, tools and software used by the company against attacks and data theft.
Security teams can use a vulnerability management tool to help identify and manage these vulnerabilities.How are vulnerabilities discovered?
The majority of vulnerabilities are indexed in the National Vulnerability Database (NVD) and have a unique identifier through the Common Vulnerabilities & Exposures (CVE) list.
To identify vulnerabilities, vulnerability scanners or automated inventory tools can be used. Scanners examine individual applications for flaws in the code and misconfigurations. Inventory tools identify the company's connected assets and their code versions. They compare these versions to the CVE vulnerability database.
Scanners often identify vulnerabilities that are not in the NVD, so it is advisable to use both types of tools to cover vulnerabilities in your organisation.
How to prioritise vulnerabilities?
The NVD also provides a regularly updated directory of vulnerabilities and CVEs, containing rankings and other additional information.
Vulnerabilities are also prioritised according to how easy it is for an attacker to exploit the vulnerability. A vulnerability in an application exposed without protection on the Internet will therefore be more urgent to correct than an internal application protected by cybersecurity tools.The stages of vulnerability management
The vulnerability management process distinguishes between several stages:
Vulnerability discovery
In order to increase the coverage of corporate vulnerabilities, it is necessary to identify the different types of security vulnerabilities.
- Configuration analysis: the tools have connectors to retrieve the configurations of the company's infrastructure elements. The tool compares the current configurations with the optimal ones in order to detect the wrong settings of the information system.
- Code audit: The tools integrate with the CI/CD to detect flawed code making applications vulnerable.
- Vulnerability scanning: Vulnerability scanners will systematically test for exposed vulnerabilities from points in the corporate network.
Prioritisation of assets
What are the company's critical assets?
Companies generally have a configuration management database (CMDB) that references assets and their characteristics (versions, dependencies, sources, targets). CMDB tools are increasingly populated with scanners that allow for a real-time inventory of all resources connected to the company's network.
It is then a matter of noting the level of criticality of the assets according to the prioritisation policies.
Prioritising vulnerabilities
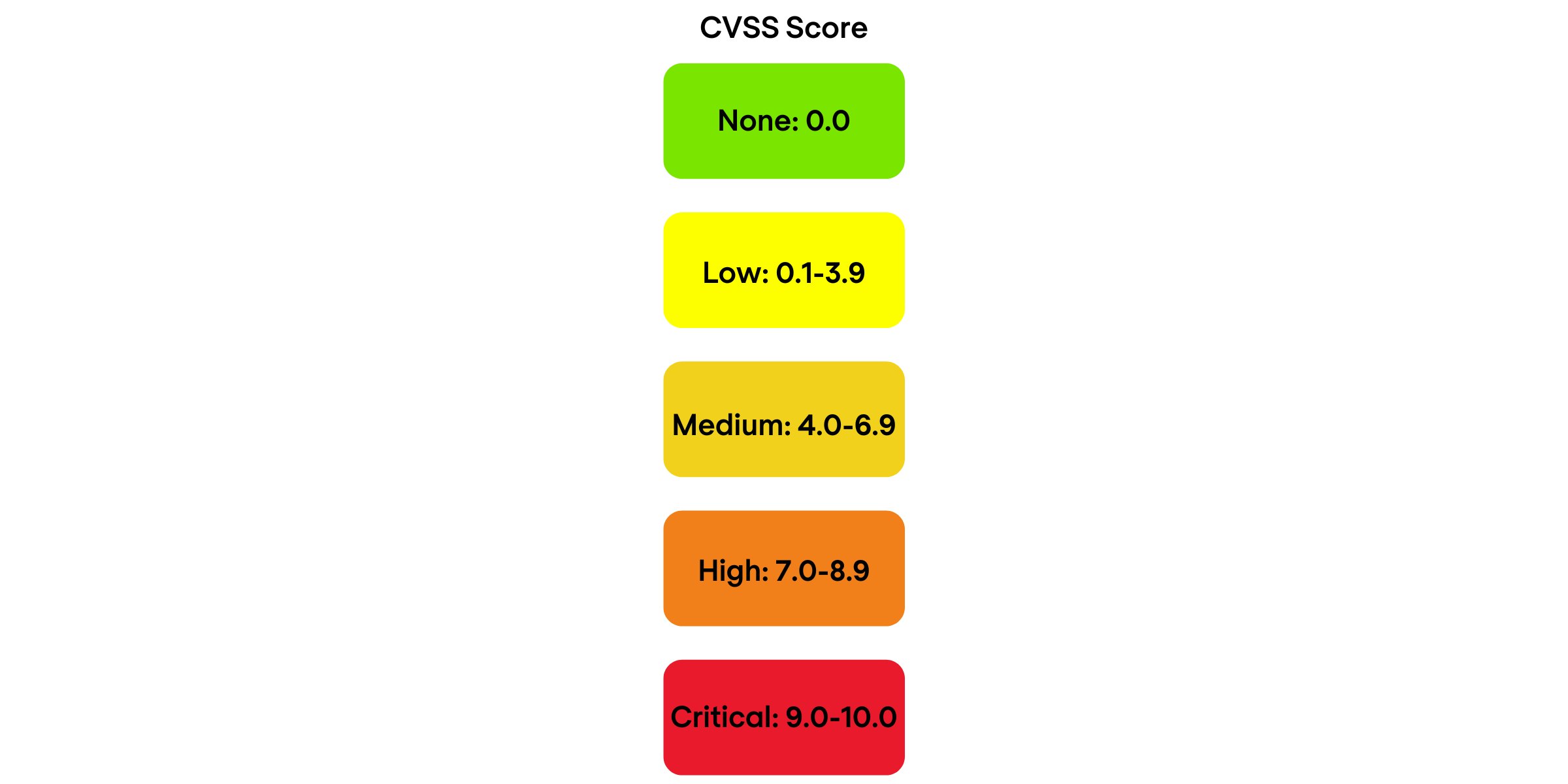
To prioritise vulnerabilities according to their level of criticality, cyber security solutions use the Common Vulnerability Scoring System (CVSS). The basic CVSS score, ranging from 0.0 to 10.0, is associated by the NVD with a severity index, as follows:
Fixing vulnerabilities
This step involves fixing or mitigating vulnerabilities. To mitigate a vulnerability, it is possible, for example, to set up configurations in the cybersecurity tools to make the vulnerability unexploitable. The vulnerability will still be present, but the likelihood of it being exploited by a malicious individual will be mitigated.
Validation of fixes
This phase is essential to verify that the fix is effective. Sometimes the fixes are not sufficient and the vulnerabilities remain effective after the supposed fix.
How many vulnerabilities do organisations typically have?
Vulnerability scans in large organisations can identify thousands of simultaneous security risks on each machine, and millions of vulnerabilities across the organisation. Research shows that almost all assets (95% of assets) contain at least one highly exploitable vulnerability.
Nomios can help you with these scans. Get expert, in-depth cybersecurity assessments to help you reduce risk, minimise breach impact, and protect against future attacks. We offer a wide range of internal and external assessments to evaluate your IT infrastructure, applications and operations, including:
- Cybersecurity assessment and analysis
- Vulnerability assessment and penetration testing
- Breach and compromise assessments
- Wireless security assessments
- Policy and procedure review and design
Our team is ready for you
Do you want to know more about this topic? Leave a message or your number and we'll call you back. We are looking forward to helping you further.
Related updates

NIS2
NIS2 requires industrial companies to make major efforts to secure their OT environments: Where to start?
Thousands of industrial companies will be affected by the implementation of NIS2, with issues varying widely from one entity to another. We present you 12 steps to achieve compliance.

Arnaud Masson

Cybersecurity Artificial Intelligence
AI in cybersecurity: A double-edged sword
AI enhances cybersecurity with quicker threat identification, proactive measures, and automated efficiency, yet presents challenges like evolving threats, ethical concerns, and a skills gap, necessitating a comprehensive defense approach.

NGFW Firewall
Top 5 NGFW solutions for 2024
Next-Generation Firewalls (NGFW) can swiftly detect and combat attacks across the entire network. As cyber-attacks continue to become more sophisticated, NGFWs will continue to be essential components of any organisation’s security solution, whether you’re in a data centre, network, or cloud.