In 1991, NASK (Naukowa i Akademicka Siec Komputerowa or Research and Academic Computer Network) connected Poland to the Internet. Today, the organization is breaking down the digital divide that prevents Polish children living in villages and towns from achieving their full academic potential. NASK manages Poland’s Nationwide Education Network (OSE), which is bringing fast, safe, and free Internet access to more than 5 million students and teachers.
“We are providing Internet connectivity and security services to all primary and secondary schools in Poland,” says Michal Mroczek, the architect of OSE and a senior network engineer at NASK.
Like many countries, Poland has a rural/urban digital divide. About 40 percent of people, including roughly 1.5 million children, live in rural areas—small towns, tiny hamlets, and remote farms. OSE aims to give these students equal digital footing for the future.
“In the big cities of Poland, Internet connectivity is good,” Mroczek says. “Our focus is on the small towns and villages where schools may have poor Internet access or none at all.”
NASK has deployed 100 Mbps Internet to 15,000 Polish schools, and all 23,000 schools across the country will be connected by the end of 2020. Beyond broadband Internet, OSE also will support students and teachers with access to content and curriculum to advance digital learning practices. Since the OSE network buildout began, bandwidth consumption at schools has doubled.
“When we started two years ago, a single school consumed about 5 Mbps of Internet bandwidth,” Mroczek says. “Now, a school consumes 10 Mbps. If you give students and teachers more Internet bandwidth, they will use more.”
The OSE Project was established to increase access to online teaching resources and eliminate areas of digital exclusion. The programme was designed by the Ministry of Digital Affairs in collaboration with the Ministry of Education under the National Education Network Act. The Act also specifies NASK (National Research Institute) as the OSE Operator, i.e. the management body.
Ensuring security for such a large network was a particularly complex project. The OSE was intended to be a public telecommunications network based on the existing broadband infrastructure developed as part of a commercial investment and subsidised by public funds. The network was to provide access to high-speed internet for teachers and students in over 80 per cent of Polish schools. This would entail high-density traffic from millions of endpoints.
The challenge
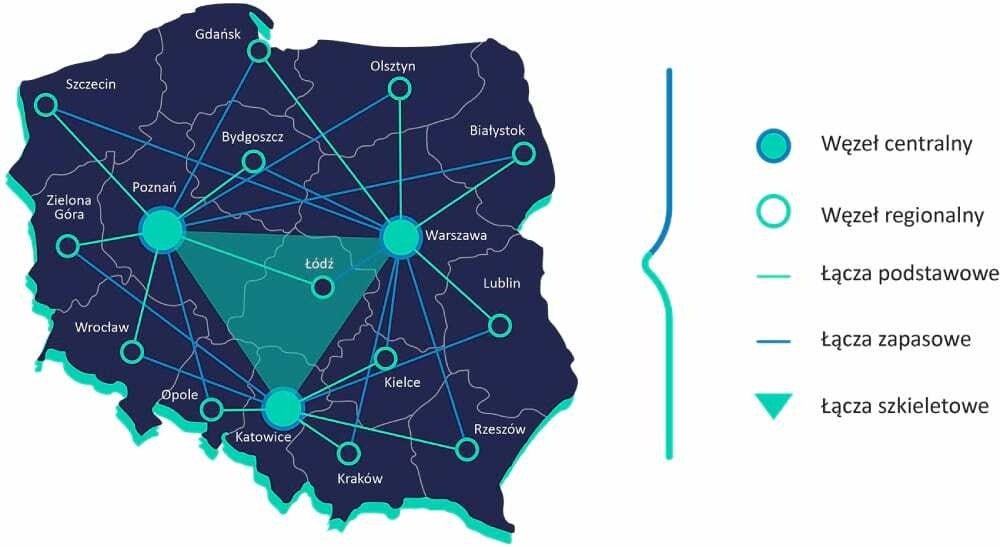
Various scenarios for the provision of security services to the OSE network were analysed during the design phase. They began with a model where all security functions are carried out at the endpoints with delivery via CPE, to a scenario where traffic is analysed in one of the 16 nodes located throughout Poland. After market consultations and months of analysis, the latter model was selected, and it was supplemented by 3 additional backbone nodes to support the services offered to the internet by the OSE network. The selection of this model has made it necessary to scale up the security systems to a level that enables traffic exceeding 1 Tbps. Various options for servicing such traffic were considered during the technical dialogue. However, many suppliers were unable to meet the requirements set for the high quality of security services, which is one of the priorities of this project. Despite this, solutions have been consistently sought to combine high-quality services with the scale of the project.
In parallel with the design work, a pilot programme was carried out to identify the characteristics of the network traffic generated by the educational establishments. According to the forecasts of the team of architects, a significant proportion of the web traffic would comprise web-based communication supported by HTTP / HTTPS protocols. The statistics gathered made it possible to observe that the share of encrypted traffic over the projected network would constitute more than 80 per cent of the total traffic handled.
Test results demonstrated that, because of the large share of encrypted traffic over the proposed network, SSL/TLS traffic interception would be necessary. This is a prerequisite for detecting threats, as well as for the proper filtering of content when accessing the internet. And through this, ensuring the high quality of security services delivered to school networks. Decryption is performed on traffic sent in both directions, which allows for analysis of enquiries and content sent over the network. Implementation of the decryption process over the operator’s network has been associated with numerous technical and organisational challenges. The biggest organisational challenge was certificate distribution across all the devices connected to the OSE network.
Scale of traffic subjected to decryption
The biggest technical challenge was the scale of traffic that would be subjected to decryption, as well as differentiation of content which should not be analysed; for example, traffic to banking, medical, and other portals. The estimated volume of OSE traffic requiring analysis amounted to more than 1 Tbps. The basic equipment within the network security system consisted of a Next-Generation Firewall (NGFW) System and a Secure Web Gateway (SWG). However, there is no equipment of this type on the market that could independently tackle such a large bandwidth when all the necessary security mechanisms are used. This indicates that a large number of NGFWs and SWGs will be required for proper decryption, analysis and re-encryption of the traffic. This would increase the complexity of the security system, as well as the cost of procuring and maintaining it.
To address this challenge, two methods of balancing the load on the security infrastructure equipment were considered. The first of these was the use of an ECMP protocol running on routers located across the OSE network. Unfortunately, during discussions with the industry, network equipment vendors flagged up significant differences in the implementation of this protocol. Some of these, such as lack of connection between incoming and outgoing traffic to/from a given user of a specific device performing SSL/TLS traffic decryption (no full TCP session visibility), prevented the delivery of all the security services on the OSE network. The given example causes that the indicated device is not able to perform the SSL/TLS traffic interception, which was one of the principles of the project described above.
The actual requirement to transfer the SSL/TLS traffic interception process from SWG and NGFW class systems to external devices was dictated by the desire to optimise the use of hardware resources in the security systems. Moreover, when NGFW and SWG kits are used, there is a requirement to control the flow of data to each device; in other words, to share the traffic. For the control to be effective, it is necessary to know the current load of each device and the routers were unable to consume this knowledge.
Because of the above considerations, the use of the ECMP protocol has been abandoned. The second model assumed the introduction of ADC class devices (Application Delivery Controller) into the OSE network. After carrying out an analysis similar to the previous one, it was assessed that all the leading products in this class were able to meet the architectural and functional objectives of the OSE network project. Moreover, ADC products provide flexibility in network traffic engineering, which was an additional advantage. The ADC shares all incoming traffic intelligently. It is the first device in the security system, and it controls the further distribution of the data flow. The above arguments were decisive in the selection of this model.
The following is the final shape of the nodes that contain the Application Delivery Controller, SSL Orchestrator, NGFW and SWG products.
The solution
The concept presented above led to the specification of the functional requirements for each of the components of the OSE. And later to a tender for a security infrastructure embracing ADC, SSLO, NGFW and DNS Firewall systems. After selection of the most advantageous bid in the tender procedure, ADC and SSLO solutions based on F5 technology were chosen. This was dictated by the following premises:
- The best ratio of SSL transactions per second (traffic decryption and re-encryption performance) concerning the physical dimensions of the devices and, consequently, their total number. The OSE network nodes had predefined maximum power values (kW) and rack space in the cabinet.
- The required performance of the Application Delivery Controllers and the ability to control traffic for a bandwidth exceeding 200 Gbps in regional nodes.
- The required flexibility of Application Delivery devices in controlling both decrypted and unencrypted traffic, including the implementation of decryption exclusions that arise either from personal data protection regulations or from a decision of the authorised personnel.
- Comprehensive protection of OSE network applications against external attacks through the use of a Web Application Firewall system.
- Enabling secure remote access for OSE network administrators or external collaborating companies using SSL and VPN technologies.
- The required integration into the maintenance environment.
“The use of the Application Delivery Controller and the SSL Orchestrators increased the simplicity of the entire OSE security system and its efficiency”, said Krzysztof Chwedorczuk, Head of the NASK Security Services Team. “F5 solutions integrate well with the other security elements and constitute one of the basic building blocks for the success of the Polish National Education Network. The implementation of the F5 technology took 5 months, which, given such a complex project, is a magnificent result”. Krzysztof Chwedorczuk added. “The OSE is constantly developing, yet so far we have not had, nor do we expect to have, any problems with load balancing within nodes or with traffic analysis”.
Summary
Industry: Education
Business challenge: Provision of access to secure broadband Internet for more than 25,000 schools in 19,500 locations across Poland.
Technology solution:
- F5 Local Traffic Manager
- F5 Application Security Manager
- F5 Access Policy Manager
- F5 SSL Orchestrator
- F5 VIPRION Series Platforms
Business result:
Secure remote access for OSE network administrators or external collaborating companies using SSL and VPN technologies
Comprehensive protection of OSE network applications against external attacks through the use of a Web Application Firewall system.

Do you have a project you would like to discuss?
Give us a call or leave a message. We are looking forward to learn about your security project, infrastructure challenges or any other inquiries.