Benefits
- Security that aligns with your top priorities
The endpoint solution you depend on should align with the priorities that matter most to you. Regardless of your role, Trellix Endpoint Security aligns to your specific critical needs—from preventing threats and hunting them to tailoring security controls. The solution enables to you to ensure system uptime for users, find more opportunities for automation, and simplify complex workflows. - Ensure Uptime and Visibility
You gain the ability to respond to and manage the threat defense lifecycle with proactive defenses and remediation tools, including returning systems to a healthy state to keep users and administrators productive, saving time that might otherwise be spent awaiting system remediation, performing recovery, or re-imaging an infected machine. - Improve protection against threats
Collaborate and accelerate the identification of suspicious behaviors, facilitate better coordination of defenses, and provide better protection against targeted attacks and zero-day threats.

Trellix Endpoint Security
- Machine learning to identify and prevent new malware
- Machine-learning behavior classification detects zero-day threats in near real time, enabling actionable threat intelligence. It automatically evolves behavior classification to identify behaviors and add rules to identify future attacks.
- Strong and Effective Performance Helps You Respond in Time
- Trellix Endpoint Security (ENS) protects the productivity of users with a common service layer and our new anti-malware core engine that helps reduce the amount of resources and power required by a user’s system. An adaptive scanning process reduces CPU demands by learning which processes, and sources are trusted to focus resources on only those that appear suspicious or that come from unknown sources.
- Centralized management with multiple deployment choices
- True centralized management offers greater visibility, simplifies operations, boosts IT productivity, unifies security, and reduces costs.
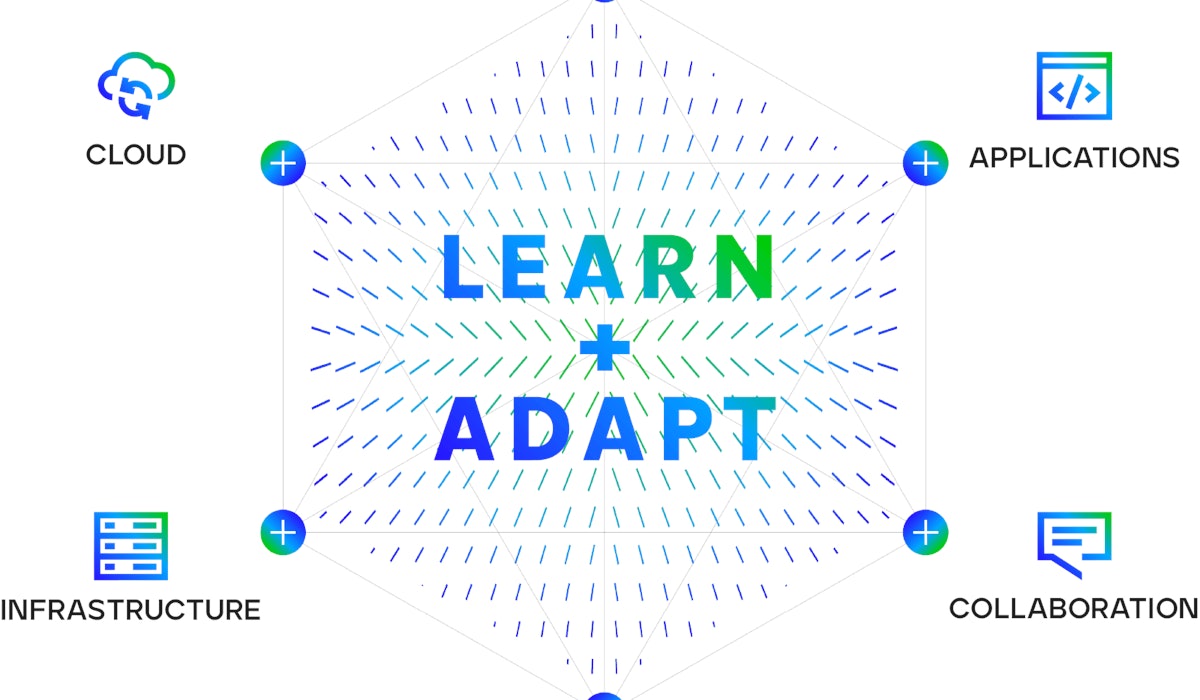
Get to know the Trellix Ecosystem
The Trellix Platform learns and adapts for living protection while delivering native and open connections and providing expert and embedded support for your team.
Ready to talk?
Are you looking for pricing details, technical information, support or a custom quote? Our team of experts in Brussels is ready to assist you.