Complete and proactive endpoint security
Empower your remote workforce to safely adopt the cloud and reduce complexity and costs with a cloud-native architecture. MVISION Endpoint Security integrates multiple technologies to defend against modern threats.
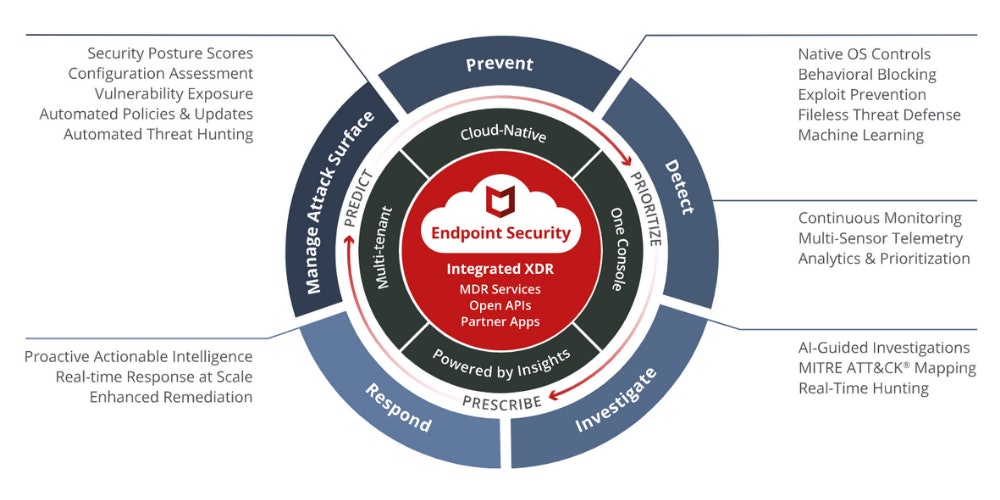
Five pillars of their endpoint security platform
Solutions
Why Endpoint Security?
McAfee Endpoint Security is built for real-time communication between threat defences. Events and threat insights are shared with multiple technologies to take immediate actions against suspicious applications, downloads, websites, and files.
Signature-less protection
Machine learning pre- and post-execution analysis
Automatic containment of suspicious executables
Integration with endpoint detection and response
One-click corrections across the entire environment
Automated workflows for greater efficiency
Features
- Centralised management
- The McAfee ePolicy Orchestrator management console can be deployed on premises or in the cloud. It provides greater visibility, simplifies operations, boosts IT productivity, unifies security, and reduces costs.
- Machine learning analysis
- Detect zero-day threats in near real time by examining how they look and behave to halt threats designed to evade detection.
- Proactive web security
- Ensure safe browsing with web protection and filtering for endpoints.
- Advanced anti-malware protection
- McAfee's anti-malware engine is continually updated by McAfee Global Threat Intelligence and works efficiently across multiple operating systems.
- Dynamic application containment
- Defend against ransomware and greyware by securing endpoints that are leveraged as entry points for attacks.
- Actionable threat forensics
- Quickly see where infections are, why they are occurring, and the length of exposure to understand the threat and react more quickly.
Ready to talk?
Are you looking for pricing details, technical information, support or a custom quote? Our team of experts in Brussels is ready to assist you.